-
Bug
-
Resolution: Not A Defect
-
Minor
-
None
-
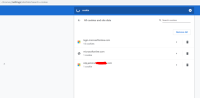
Jenkins LTS 2.176.2
saml:1.1.2 SAML Plugin
Issue
The logout button does not work as expected. The SAML session is not finished
Steps
0.- Configuring SAML by using Azure as IdP Provider following:
- https://github.com/jenkinsci/saml-plugin/blob/master/doc/CONFIGURE_AZURE.md
- https://github.com/jenkinsci/saml-plugin/blob/master/doc/TROUBLESHOOTING.md#azure-ad
> The max lifetime of the Access Token in Azure AD seems to be 24 hours where the refresh token can live for a maximum of 14 days (if the access token expires the refresh token is used to try to obtain a new access token). The Jenkins setting in Configure Global Security > SAML Identity Provider Settings > Maximum Authentication Lifetime is 24 hours (86400 in seconds) upping this to 1209600 (which is 14 days in seconds/the max lifetime of the Refresh Token).
1.- Log in to Jenkins, it redirects you to the SAML SSO... you log in. Thus, everything works as expected. The following cookies are created
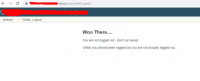
2.- Try to Log out from Jenkins, the message is correct. Bt You are still logged into Jenkins then you can browse along with the instance.
3.- Try to Log into Jenkins again and then you get this error.
Independently of the error, you are still logged into Jenkins
How to log out
Deleting the cookies directly from the Browser. Having done that, if you try to access again, you are redirected toAzure to Login again.
Custom logs
Following https://github.com/jenkinsci/saml-plugin/blob/master/doc/TROUBLESHOOTING.md#troubleshooting
I don't find any issue with the doFinishLogin. It seems to me like session.invalidate() is not working... Am I missing anything?
2019-09-26 11:06:01.467+0000 [id=11965] FINER o.j.p.saml.SamlSecurityRealm#doFinishLogin: SamlSecurityRealm.doFinishLogin called 2019-09-26 11:06:01.467+0000 [id=11965] FINEST o.j.p.saml.SamlSecurityRealm#recreateSession: Invalidate previous session 2019-09-26 11:06:01.469+0000 [id=11965] FINEST o.j.p.saml.SamlSecurityRealm#logSamlResponse: SAMLResponse XML:<samlp:Response ID="_e9685df9-eccd-4bce-a1d1-b1db033f08c5" Version="2.0" IssueInstant="2019-09-26T11:06:01.248Z" Destination="https://s2p-jenkins.opuscapita.com/cjoc/securityRealm/finishLogin" InResponseTo="_l17diieuwupjb9vdamon7wvlg0sclszq134kyju" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"><Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">https://sts.windows.net/91e00cb2-b7c0-41b8-aa04-bbd40d719dee/</Issuer><samlp:Status><samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status><Assertion ID="_fbe70e20-38c5-4019-9a23-865a5a653f00" IssueInstant="2019-09-26T11:06:01.238Z" Version="2.0" xmlns="urn:oasis:names:tc:SAML:2.0:assertion"><Issuer>https://sts.windows.net/91e00cb2-b7c0-41b8-aa04-bbd40d719dee/</Issuer><Signature xmlns="http://www.w3.org/2000/09/xmldsig#"><SignedInfo><CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/><SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/><Reference URI="#_fbe70e20-38c5-4019-9a23-865a5a653f00"><Transforms><Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></Transforms><DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/><DigestValue>85Ww20J9x1KzAhKcw0FpKtnKuSSq8fpnLRLmYu2e0NE=</DigestValue></Reference></SignedInfo><SignatureValue>YFecfrXbRYKnx1CVDmaiTszLPKPYZ0y3O9cShy1DpndJI47dnhtyIvS3S1InWn7PgcE/XT4Dr49o4XF1VAAgoCsPJYygOiYKx2+KKd2vpfEYCNX0ugqpOyIjOLmUQ4zJzl+kYbJJue15LWv7bQQJ2Dv92W7BeY6xVEsuuCvV/Yf74ycPU0N+gjFBqne1m22PhxWbOSMrARLhB06NIiim7Ii2QbXHpO7PsbxJqkuHTyLWKM3M2lEdeUKpqo/mX6w0MnZCvDpMvST/52YL3uUvmK14i5H7tCzCh2OXGAFgoOTKQUVgFFm0IvuVkZCNodOqlpTDCeNFtHLjaogT8cDmug==</SignatureValue><KeyInfo><X509Data><X509Certificate>MIIDBTCCAe2gAwIBAgIQU10WcpDECatD1ywgv0TNJjANBgkqhkiG9w0BAQsFADAtMSswKQYDVQQDEyJhY2NvdW50cy5hY2Nlc3Njb250cm9sLndpbmRvd3MubmV0MB4XDTE5MDgyNTAwMDAwMFoXDTI0MDgyNDAwMDAwMFowLTErMCkGA1UEAxMiYWNjb3VudHMuYWNjZXNzY29udHJvbC53aW5kb3dzLm5ldDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKdg88TmYlhB4bVWr7sCJq8k0cVuJCdJmwNZW16J+edA1Jyg2QjWWs7Z6PB6TpejUm1W1vkCw8+VTqgp/jw70iEXMPtoayT0ZwjaG+MhhLgu7/XT1aTwxUYlKznMAmyWpOsbCvTxLF/BUP6JxRzumCZI7BRvEtpzIYESviXVEVHLo/aWssEgbVvXXXqo0D4Aj22SbZN/UXqLqAWDZvcYsIUzdCJ2PUbfTylIeHEXrYNznikNhPEzlYdZx3k09hyCGJwIAexElANO8GAbr3reFBnpgtknX6U0lpNmKs42TjVvKdNYSYPcfJXEnsmkFTsUz/0o0KD/fZWtVfJQKxd+asUCAwEAAaMhMB8wHQYDVR0OBBYEFPBE/OYhU7DwWnEa6luL8L+MZwbHMA0GCSqGSIb3DQEBCwUAA4IBAQAYyA81g/dfsm/AeUyDfzObRaEdKinKI5GUFUvJXDobED7f6NL+ECyULBEVm/ksZBrg6f0aPTDnSFVsZIfMogXc0KfJrII1lnXucbt1LCOmjdlf54J1R/mn9dkHyZ3pfoZtpqcXlKFnRCurn864XqRQFgBSG39xUjXXUR5vWSrp3mHlil+W9Z9RTImNmkXnSJDosYLEvCUYyqarV8rKj6rBfaBdqP3F5s4GwIdjsZ13YfkD4c+meX3W/9x74awB5ys+p78c7IjnO8mQB9kPvY9wEnGLDfLQEC+A0af81ybvevMraFfwZtsq/FYJEMnn6hKkTUeb1kPpVdJLVN4JqiUM</X509Certificate></X509Data></KeyInfo></Signature><Subject><NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent">Z3xgevzWMo9EjHqquVdhuLluC7nujZpFNMZ9gQ1jI4E</NameID><SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><SubjectConfirmationData InResponseTo="_l17diieuwupjb9vdamon7wvlg0sclszq134kyju" NotOnOrAfter="2019-09-26T11:11:01.238Z" Recipient="https://s2p-jenkins.opuscapita.com/cjoc/securityRealm/finishLogin"/></SubjectConfirmation></Subject><Conditions NotBefore="2019-09-26T11:01:01.238Z" NotOnOrAfter="2019-09-26T12:06:01.238Z"><AudienceRestriction><Audience>api://603e0ec5-caba-4cda-9b4b-ef108f272b23</Audience></AudienceRestriction></Conditions><AttributeStatement><Attribute Name="http://schemas.microsoft.com/identity/claims/tenantid"><AttributeValue>91e00cb2-b7c0-41b8-aa04-bbd40d719dee</AttributeValue></Attribute><Attribute Name="http://schemas.microsoft.com/identity/claims/objectidentifier"><AttributeValue>ca68de19-5b5d-43e5-9061-39ff3e9efe3d</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"><AttributeValue>Amit.Tiwari@opuscapita.com</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname"><AttributeValue>Tiwari</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname"><AttributeValue>Amit</AttributeValue></Attribute><Attribute Name="http://schemas.microsoft.com/identity/claims/displayname"><AttributeValue>Tiwari Amit</AttributeValue></Attribute><Attribute Name="http://schemas.microsoft.com/ws/2008/06/identity/claims/groups"><AttributeValue>aaafebc1-649c-4ccd-8b38-1e8098f0bb7e</AttributeValue><AttributeValue>bad2bc59-5af3-4ef4-a96f-e0012b7814cb</AttributeValue><AttributeValue>3f308155-20b5-4a97-b2a1-298a8f713df2</AttributeValue><AttributeValue>ea44c7c8-1018-4736-a546-64ac199c906d</AttributeValue><AttributeValue>8e07f9df-3061-4bf2-be1d-7c587f7453dc</AttributeValue><AttributeValue>5c574fda-7edf-4c09-94dd-f7c89b6cde61</AttributeValue><AttributeValue>3c19a7be-f323-4b81-845e-fc4a21c8dd64</AttributeValue><AttributeValue>29f20cad-759a-437b-8713-04af4c8cfc87</AttributeValue><AttributeValue>1cb6c98b-8528-450a-b160-b4bd924f3d64</AttributeValue><AttributeValue>48d84205-c46b-46fb-9281-e7da83faf8e4</AttributeValue><AttributeValue>1d4aeaf6-0793-4753-b3c4-1ae08a4e40d4</AttributeValue><AttributeValue>490bd912-f143-49a6-9c93-82c8d95520ac</AttributeValue><AttributeValue>2eb13724-484c-4907-b219-f4f3c1c03681</AttributeValue><AttributeValue>98551470-0fec-4262-9636-5171d6d0688d</AttributeValue><AttributeValue>c62e1e61-940c-46f9-b76f-b8a8cd21c695</AttributeValue><AttributeValue>b5f0dd56-a5e8-4010-9020-5bb89b0c8423</AttributeValue><AttributeValue>52504ac1-27fa-4ac9-b7f9-96314c6822d6</AttributeValue><AttributeValue>e52115a2-4b8b-45aa-a96c-a818fb3b35db</AttributeValue><AttributeValue>9b1665c4-80bc-4c07-a470-3ce655f6fa3b</AttributeValue><AttributeValue>851c301f-f3cb-4815-b21a-e6607629b39b</AttributeValue></Attribute><Attribute Name="http://schemas.microsoft.com/identity/claims/identityprovider"><AttributeValue>https://sts.windows.net/91e00cb2-b7c0-41b8-aa04-bbd40d719dee/</AttributeValue></Attribute><Attribute Name="http://schemas.microsoft.com/claims/authnmethodsreferences"><AttributeValue>http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password</AttributeValue></Attribute></AttributeStatement><AuthnStatement AuthnInstant="2019-09-26T11:05:56.678Z" SessionIndex="_fbe70e20-38c5-4019-9a23-865a5a653f00"><AuthnContext><AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClassRef></AuthnContext></AuthnStatement></Assertion></samlp:Response> 2019-09-26 11:06:01.470+0000 [id=11965] FINEST o.j.plugins.saml.OpenSAMLWrapper#get: adapt TCCL