-
Bug
-
Resolution: Unresolved
-
Minor
-
None
-
* Jenkins 2.289.3
* Shelve Project Plugin 3.2
In the following scenario:
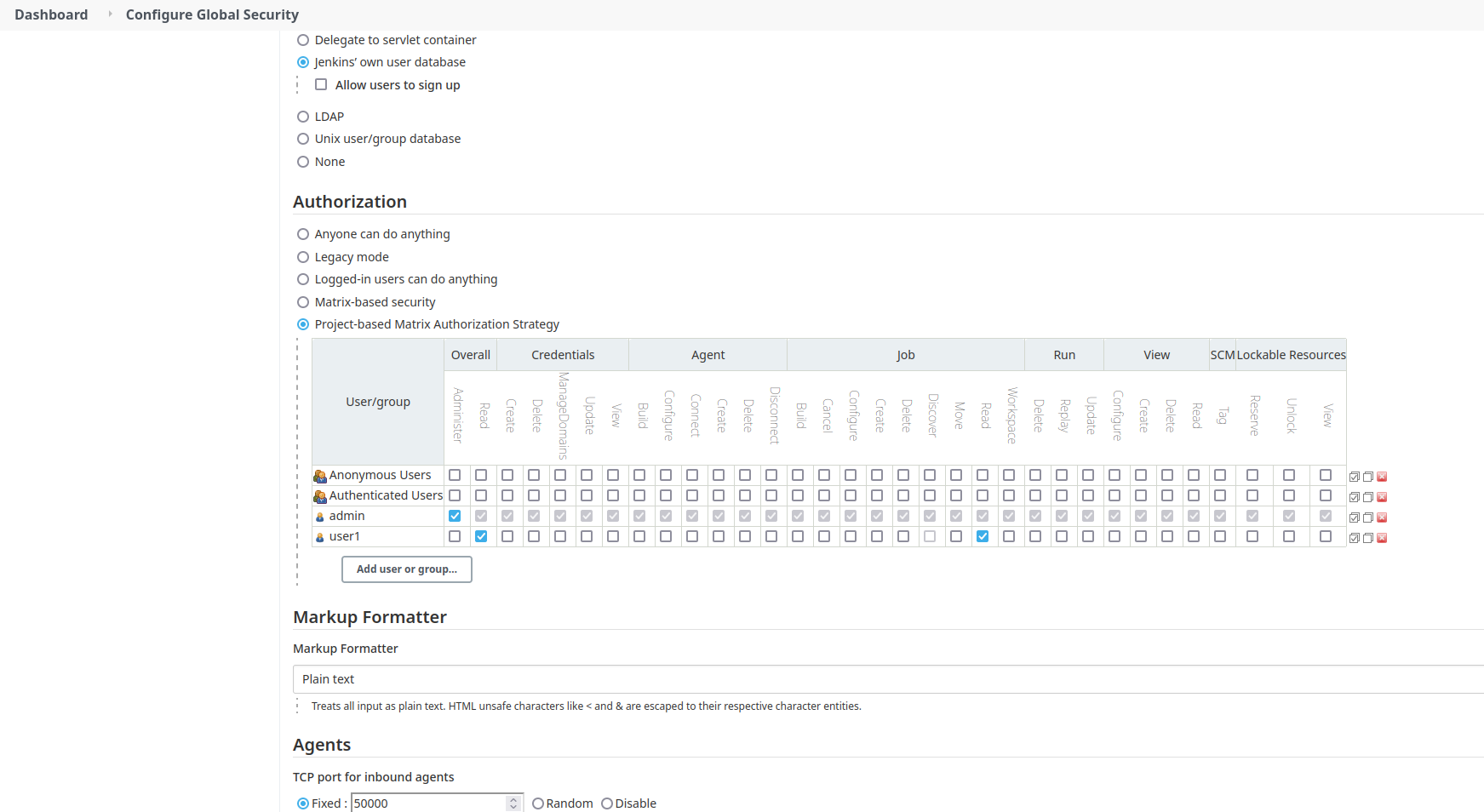
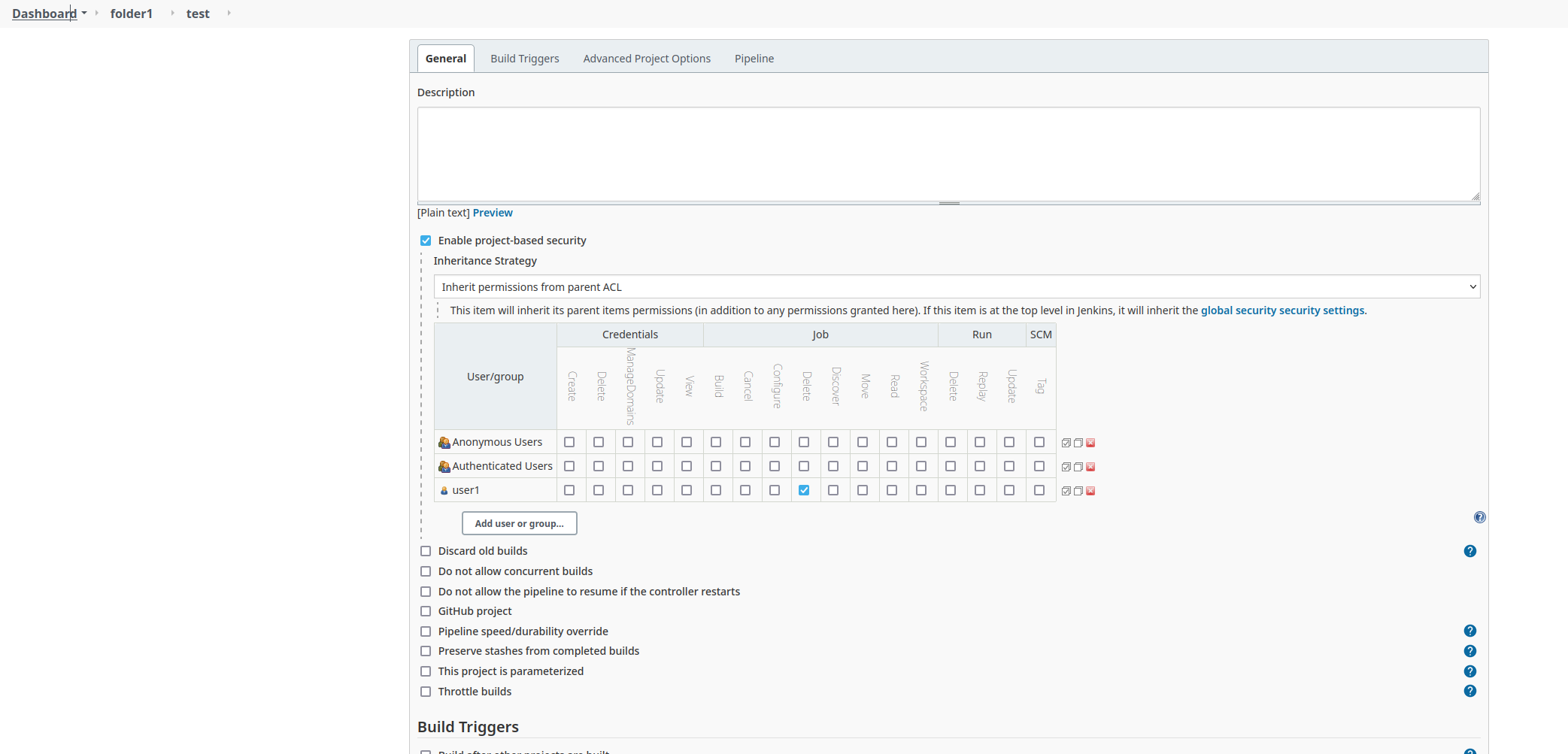
- Choose `Project-based Matrix Authorization Strategy` Athorization strategy (and other like Role-Base strategy)
- `user1` without the `job - delete` permission at the Jenkins root level.
- `user1` with `job - delete` permission at the project (pipeline) level.
The user is able to see the `delete project` link but not the `shelve project` link.
Reviewing the source code, I found the following line:
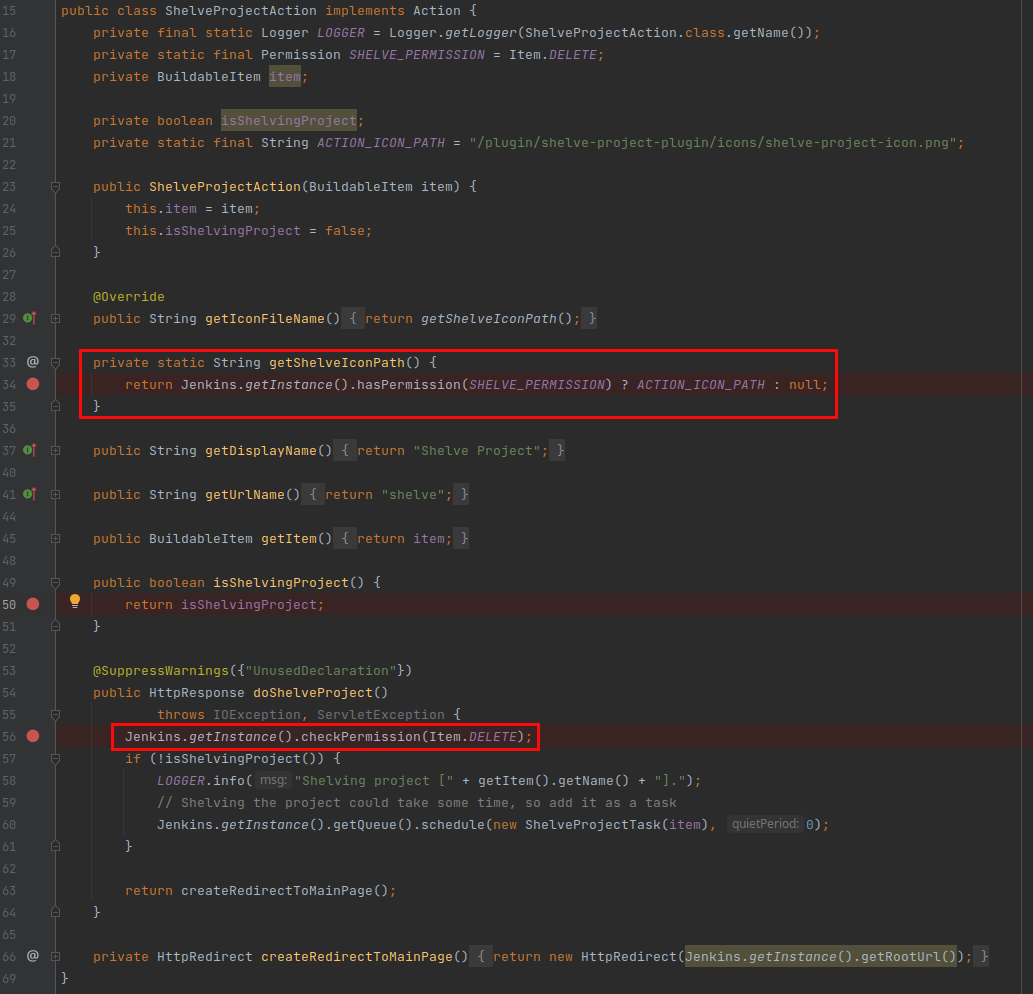
I believe the item that is currently visited should be checked and not the `Jenkins.getInstance()` item.
This problem force us to grant job - deleting permission for all project if we want to shelve only one project.
[JENKINS-66382] Job - Delete permission at Jenkins root level is needed to shelve the project
| Link | New: This issue relates to JENKINS-66419 [ JENKINS-66419 ] |
| Status | Original: Open [ 1 ] | New: In Progress [ 3 ] |




![freestyle [folder1] [Jenkins] — Mozilla Firefox (Private Browsing)_216.png](https://issues.jenkins.io/secure/thumbnail/56202/_thumb_56202.png)
![freestyle [folder1] [Jenkins] - Google Chrome_218.png](https://issues.jenkins.io/secure/thumbnail/56204/_thumb_56204.png)
![pipeline [folder1] [Jenkins] - Google Chrome_219.png](https://issues.jenkins.io/secure/thumbnail/56205/_thumb_56205.png)
![Assign Roles [Jenkins] — Mozilla Firefox_215.png](https://issues.jenkins.io/secure/thumbnail/56201/_thumb_56201.png)
![Manage Roles [Jenkins] — Mozilla Firefox_214.png](https://issues.jenkins.io/secure/thumbnail/56200/_thumb_56200.png)
![freestyle [folder1] [Jenkins] - Google Chrome_224.png](https://issues.jenkins.io/secure/thumbnail/56210/_thumb_56210.png)
![freestyle [folder1] [Jenkins] — Mozilla Firefox (Private Browsing)_226.png](https://issues.jenkins.io/secure/thumbnail/56212/_thumb_56212.png)
![pipeline [folder1] [Jenkins] - Google Chrome_225.png](https://issues.jenkins.io/secure/thumbnail/56211/_thumb_56211.png)
![pipeline [folder1] [Jenkins] — Mozilla Firefox (Private Browsing)_217.png](https://issues.jenkins.io/secure/thumbnail/56203/_thumb_56203.png)
![pipeline [folder1] [Jenkins] — Mozilla Firefox (Private Browsing)_227.png](https://issues.jenkins.io/secure/thumbnail/56213/_thumb_56213.png)
![Configure Global Security [Jenkins] — Mozilla Firefox_220.png](https://issues.jenkins.io/secure/thumbnail/56206/_thumb_56206.png)
![Configure Global Security [Jenkins] — Mozilla Firefox_221.png](https://issues.jenkins.io/secure/thumbnail/56207/_thumb_56207.png)
![freestyle Config [Jenkins] — Mozilla Firefox_222.png](https://issues.jenkins.io/secure/thumbnail/56208/_thumb_56208.png)
![pipeline Config [Jenkins] — Mozilla Firefox_223.png](https://issues.jenkins.io/secure/thumbnail/56209/_thumb_56209.png)
ironcerocloudbees while not ideal, this is currently done so by design for simplicity sake when developing
JENKINS-27734(which introduced the possibility to shelve any kind of item, including containers (eg folder)).The issue with what you are proposing is that it would rely on the authorization scheme to inherit rights to children items which is not necessarily true, eg with the Project-based Matrix Authorization Strategy, one strategy is:
What this means is that you can have delete permission on an item, yet not have it on a child item. I'm not sure how Jenkins reconcile this, I'll need to mount a test environment and run some tests to understand the behavior of the delete action in Jenkins.