Hi Team,
We could see YUI has been detected with vulnerabilities that is available under jenkins installation directory.
When we checked security team, they have given below screenshot as vulnerable
Currently we are on 2.401.3 and this is almost latest version. Could you please let us know how to get rid of this vulnerabilities.
i selected the components as security inspector as i could not find yui

[JENKINS-72465] Outpost24 security scanner incorrectly reports a YUI security vulnerability in Jenkins 2.401.3
| Assignee | Original: sudheer kumar [ sudheerkumar93 ] |
| Component/s | New: core [ 15593 ] | |
| Component/s | Original: security-inspector-plugin [ 21938 ] | |
| Labels | New: yui |
| Summary | Original: Security vulnerability still shows even after update to 2.401.3 | New: Security scanner incorrectly reports a YUI security vulnerability in Jenkins 2.401.3 |
| Resolution | New: Not A Defect [ 7 ] | |
| Status | Original: Open [ 1 ] | New: Resolved [ 5 ] |
| Summary | Original: Security scanner incorrectly reports a YUI security vulnerability in Jenkins 2.401.3 | New: Outpust24 security scanner incorrectly reports a YUI security vulnerability in Jenkins 2.401.3 |
| Summary | Original: Outpust24 security scanner incorrectly reports a YUI security vulnerability in Jenkins 2.401.3 | New: Outpost24 security scanner incorrectly reports a YUI security vulnerability in Jenkins 2.401.3 |
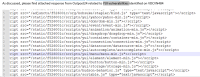
Note that YUI currently which is available in the installation directory has reached end of life and the suggestion is to upgrade to newer supported version.
Could you please let us know in which version of jenkins this YUI has been updated to latest support version.