-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Minor
-
Component/s: bitbucket-branch-source-plugin
-
None
-
934.4.2
Related to https://issues.jenkins.io/browse/JENKINS-75184
I am still unable to list credentials when creating or updating a Jenkins multibranch pipeline using Bitbucket Branch Source Plugin. I have this issue since version 933.0.1, so the last valid version was 932.vff504b_2003fe. There is no error log in system logs. On the other hand, we lost the build notifications in the PRs, this feature was fixed on 933.2.1 but we can't upgrade to that version because of the problem described in this ticket.
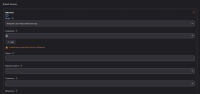
As you can see in the following image, the credentials' dropdown keeps waiting

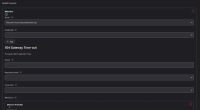
Until I get a 504 Gateway timeout.

- is related to
-
JENKINS-75184 CredentialsMatcher fail with ECR Security Token
-
- Closed
-
- links to