-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Blocker
-
Component/s: bitbucket-branch-source-plugin
-
Environment:Jenkins core:
- 2.100
- Experimental update center enabled
Git and Bitbucket plugins:
- github 1.28.1
- cloudbees-bitbucket-branch-source 2.2.8
- git-server 1.7
- blueocean-github-pipeline 1.4.0-beta-4
- git-client 2.7.0
- github-branch-source 2.3.2
- blueocean-git-pipeline 1.4.0-beta-4
- github-api 1.90
- blueocean-bitbucket-pipeline 1.4.0-beta-4
- git 3.7.0
- pipeline-github-lib 1.0
Pipeline plugins:
- workflow-job 2.17-durability-beta-1
- workflow-durable-task-step 2.17
- workflow-step-api 2.14
- workflow-support 2.17-durability-beta-1
- workflow-multibranch 2.17-durability-beta-1
- workflow-cps 2.43-durability-beta-1
- workflow-cps-global-lib 2.9
- workflow-basic-steps 2.6
- workflow-aggregator 2.5
- workflow-scm-step 2.6
- workflow-api 2.25-durability-beta-2
- docker-workflow 1.14
Client:
- Fedora Workstation 27
- Updated as of about a day ago
- Google Chrome Version 63.0.3239.108 (Official Build) (64-bit)Jenkins core: - 2.100 - Experimental update center enabled Git and Bitbucket plugins: - github 1.28.1 - cloudbees-bitbucket-branch-source 2.2.8 - git-server 1.7 - blueocean-github-pipeline 1.4.0-beta-4 - git-client 2.7.0 - github-branch-source 2.3.2 - blueocean-git-pipeline 1.4.0-beta-4 - github-api 1.90 - blueocean-bitbucket-pipeline 1.4.0-beta-4 - git 3.7.0 - pipeline-github-lib 1.0 Pipeline plugins: - workflow-job 2.17-durability-beta-1 - workflow-durable-task-step 2.17 - workflow-step-api 2.14 - workflow-support 2.17-durability-beta-1 - workflow-multibranch 2.17-durability-beta-1 - workflow-cps 2.43-durability-beta-1 - workflow-cps-global-lib 2.9 - workflow-basic-steps 2.6 - workflow-aggregator 2.5 - workflow-scm-step 2.6 - workflow-api 2.25-durability-beta-2 - docker-workflow 1.14 Client: - Fedora Workstation 27 - Updated as of about a day ago - Google Chrome Version 63.0.3239.108 (Official Build) (64-bit)
Summary:
On a Jenkins instance where Security is set to "Logged in users can do anything," the logged in user admin is shown Access Denied: admin is missing the Job/Configure permission when viewing repositories inside of a Bitbucket Team project. At the same time this is shown, the Jenkins log shows a hudson.security.AccessDeniedException2.
Steps to recreate:
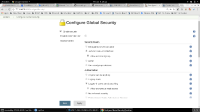
1. Go to Global Security, and set it to "Logged-in users can do anything."
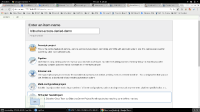
2. Set up a Bitbucket Team/Project job:
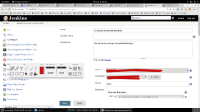
3. Go through the Configuration screen and set up the project in a normal way:
4. Verify that the project has been created:
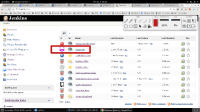
5. Verify that you can at least run some builds for repos inside of this Team Project. In this case I'm looking at a particular branch:
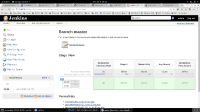
6. (Optional) If you have shell access to the instance, tail -f the Jenkins log.
7. Go back up to the top level of the project, select the drop down next to one of the repositories, and pick "View Configuration:"
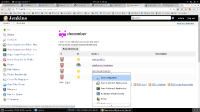
8. In the Branch Sources section, directly under the "Repository Name" pulldown, notice there's sort of a second Jenkins UI being shown, which says "Access Denied."
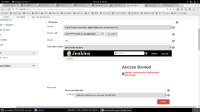
9. The Jenkins log will display the following information on loading the View Configuration page:
Jan 05, 2018 7:25:45 PM org.eclipse.jetty.server.handler.ContextHandler$Context log INFO: While serving http://172.18.40.95:8080/job/bitbucket-access-denied-demo/job/test-of-pull-requests/descriptorByName/com.cloudbees.jenkins.plugins.bitbucket.BitbucketSCMSource/fillRepositoryItems: hudson.security.AccessDeniedException2: admin is missing the Job/Configure permission
This is an issue for two reasons. First, there shouldn't be this second UI at all. Second, it's not clear why a logged-in user on a system which has been set to "Logged in users can do anything" would be denied access to anything
- links to