-
Type:
Bug
-
Resolution: Won't Do
-
Priority:
Minor
-
Component/s: splunk-devops-plugin
-
None
Hello,
I am having difficulties hiding sensitive information from Jenkins console log when sending to Splunk using splunk-devops* plugins and Splunk App for Jenkins.
I tried using both ways of handling credentials in Jenkins (https://jenkins.io/doc/book/pipeline/jenkinsfile/#handling-credentials), using declarative pipeline with:
- credentials() helper method in environment section, credentials type Username with password
- withCredentials step in stage, credentials type Username with password
If used within the pipeline the information does not get propagated to Splunk (which is probably OK).
If used in conjunction with for example the 'sh' step, in the first case, the credentials are propagated in plaintext to Splunk, in second case only asterisks (as expected) are propagated:
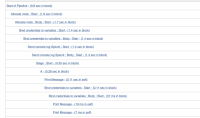
(Output from Splunk![]()
| 1569315490.309 | 2019-09-24T08:58:10.309+0000 + echo 'Username and Password: myusername:mysecretpassword' |
| 1569315490.309 | 2019-09-24T08:58:10.309+0000 Username and Password: myusername:mysecretpassword |
| 1569315490.636 | 2019-09-24T08:58:10.636+0000 + echo 'Username: ****' |
| 1569315490.636 | 2019-09-24T08:58:10.636+0000 Username: **** |
| 1569315490.910 | 2019-09-24T08:58:10.910+0000 + echo 'Password: ****' |
| 1569315490.910 | 2019-09-24T08:58:10.910+0000 Password: **** |
When inspecting the Jenkins console log (see attachment), credentials are properly masked as expected.
Am I using it wrong? Is the plugin compatible only with "withCredentials" step?
Thank you for your help.