-
Type:
Bug
-
Resolution: Duplicate
-
Priority:
Major
-
Component/s: _unsorted
-
Environment:Jenkins ver. 2.204.2
Azure VM Agents 1.4.0
Hi!
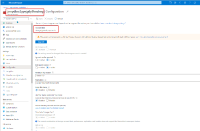
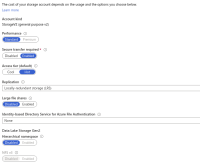
We are trying to use the plugin with an existing resource group and storage account but this is not working with one of our subscription because of a policy that force "secure transfer" enabled.
The storage account is already configured with secure transfer, but it seems that the plugin is trying to "change" the configuration of the storage account. Which fail with following error.
Same issue if trying to use a new storage account
This prevent us using the plugin ![]()
Is it possible for example to have an option on the config to force the use of secure transfer and avoid issue with policies ?
AzureVMManagementServiceDelegate: deployment: Unable to deploy
com.microsoft.azure.CloudException: Status code 400, {"error":{"code":"InvalidTemplateDeployment","message":"The template deployment failed because of policy violation. Please see details for more information.","details":[{"code":"RequestDisallowedByPolicy","target":"*********","message":"Resource '*****devop*****jenkins******' was disallowed by policy. Policy identifiers: '[{\"policyAssignment\":{\"name\":\"Secure transfer to storage accounts should be enabled\",\"id\":\"/subscriptions/*********/providers/Microsoft.Authorization/policyAssignments/***********\"},\"policyDefinition\":{\"name\":\"Secure transfer to storage accounts should be enabled\",\"id\":\"/providers/Microsoft.Authorization/policyDefinitions/************\"}},{\"policyAssignment\":{\"name\":\"Secure transfer to storage accounts should be enabled\",\"id\":\"/providers/Microsoft.Management/managementGroups/********-***-mg/providers/Microsoft.Authorization/policyAssignments/************\"},\"policyDefinition\":{\"name\":\"Secure transfer to storage accounts should be enabled\",\"id\":\"/providers/Microsoft.Authorization/policyDefinitions/*************\"}}]'.","additionalInfo":[{"type":"PolicyViolation","info":{"policyDefinitionDisplayName":"Secure transfer to storage accounts should be enabled","evaluationDetails":{"evaluatedExpressions":[{"result":"True","expressionKind":"Field","expression":"type","path":"type","expressionValue":"Microsoft.Storage/storageAccounts","targetValue":"Microsoft.Storage/storageAccounts","operator":"Equals"},
Thanks in advance for the help!
Valentin
- relates to
-
JENKINS-52967 Add support for https storage account
-
- Resolved
-