-
Type:
Bug
-
Resolution: Unresolved
-
Priority:
Minor
-
Component/s: shelve-project-plugin
-
None
-
Environment:* Jenkins 2.289.3
* Shelve Project Plugin 3.2
In the following scenario:
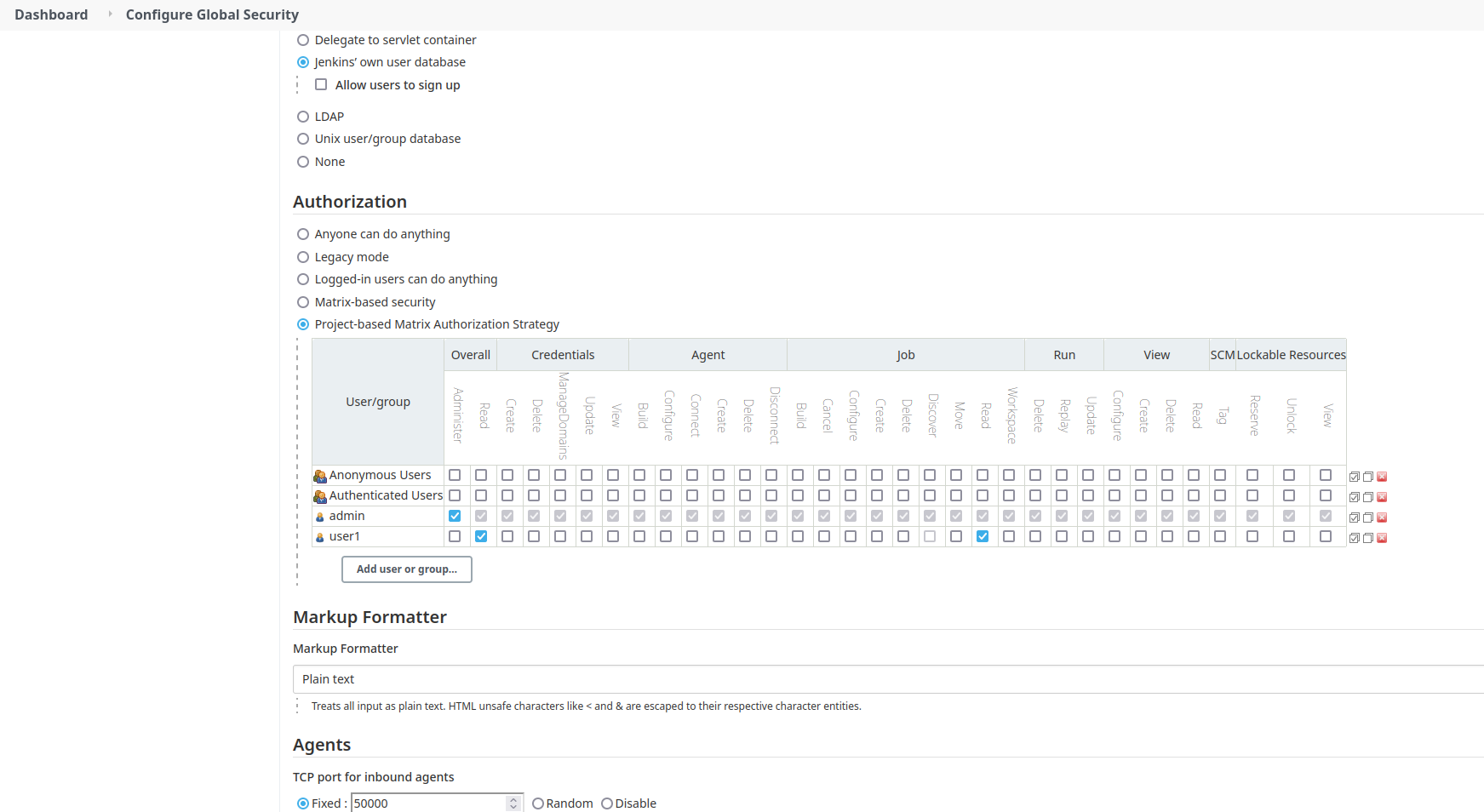
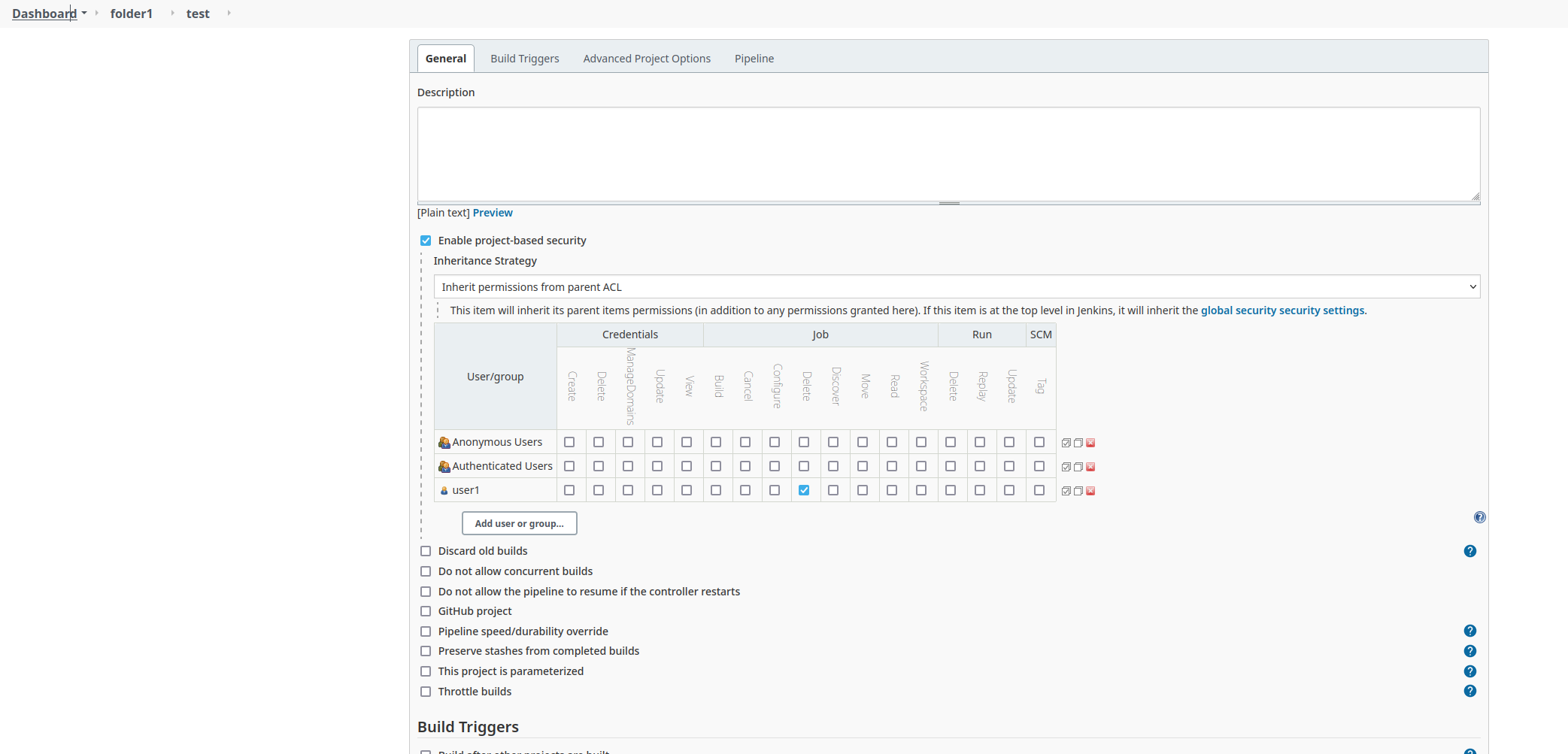
- Choose `Project-based Matrix Authorization Strategy` Athorization strategy (and other like Role-Base strategy)
- `user1` without the `job - delete` permission at the Jenkins root level.
- `user1` with `job - delete` permission at the project (pipeline) level.
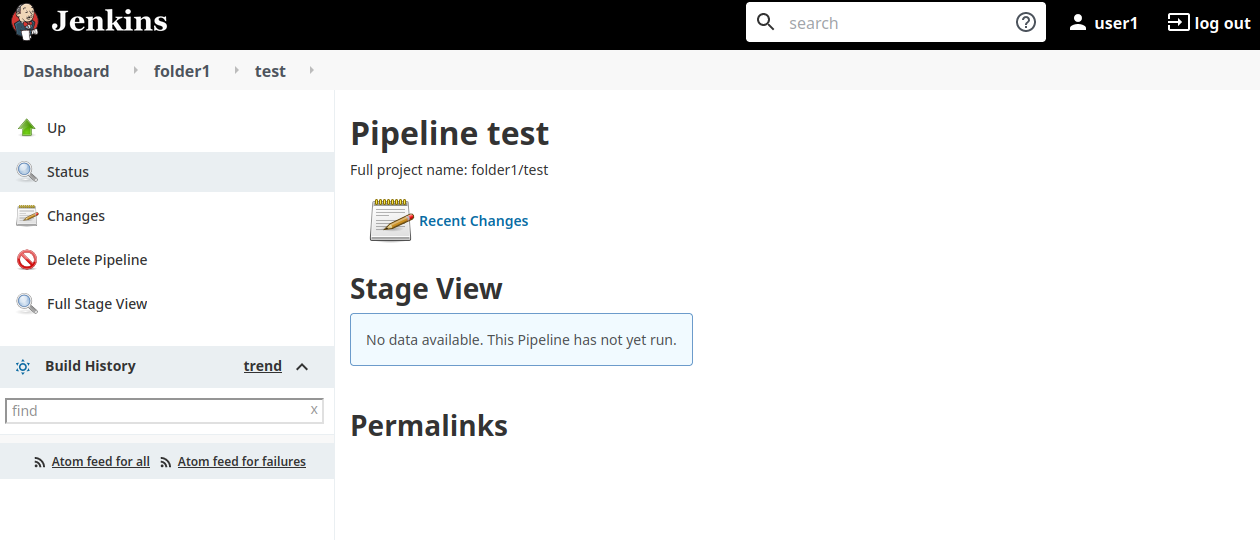
The user is able to see the `delete project` link but not the `shelve project` link.
Reviewing the source code, I found the following line:
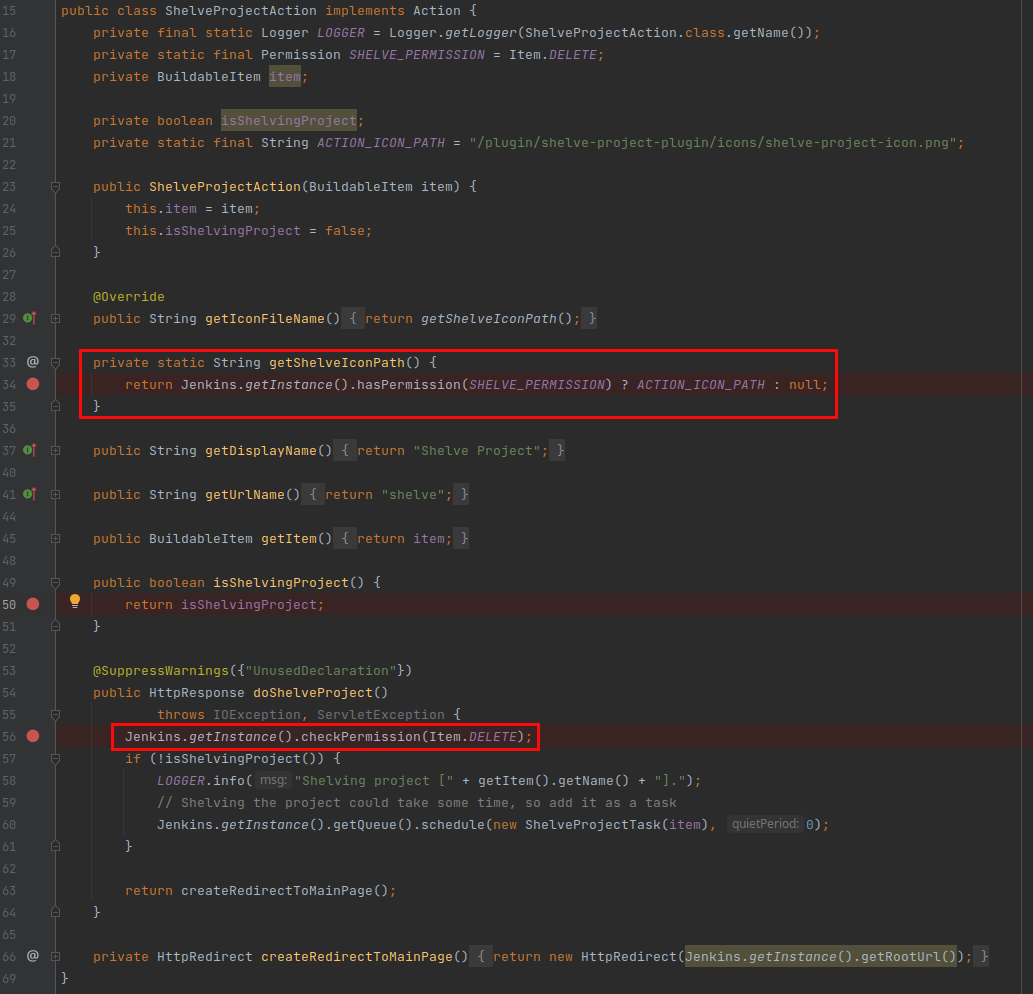
I believe the item that is currently visited should be checked and not the `Jenkins.getInstance()` item.
This problem force us to grant job - deleting permission for all project if we want to shelve only one project.