-
Type:
Bug
-
Resolution: Not A Defect
-
Priority:
Minor
-
Component/s: saml-plugin
-
None
-
Environment:Jenkins 2.346.3 via Docker (jenkins/jenkins:lts-jdk11)
I've recently implemented the SAML plugin on a Jenkins test setup for use with Azure AD. This setup is in docker and is basically nothing but a SAML configuration.
Sign in works fine and as expected, but logging out results in an error. I see no configuration I could do on Azure AD to fix the issue and nothing maligned in my configuration.
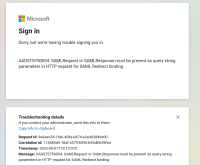
This is the response Azure AD returns on the call. This coincides with the attached screenshot. Azure AD reports this request as 'interrupted'.
Request URL: https://login.microsoftonline.com/removed-url/saml2Request
Method: GET
Status Code: 400 Bad Request
Remote Address: removed-ip:443
Referrer Policy: same-origin
I see no query parameters defined in the URL for SAMLRequest or SAMLResponse.
The logout call in the network tab also reports this, followed by the actual saml request above.
http://localhost:8080/logout Request Method: GET Status Code: 302 Found Remote Address: [::1]:8080 Referrer Policy: same-origin Location: https://login.microsoftonline.com/removed-url/saml2
This is the configuration with important info removed:
<?xml version='1.1' encoding='UTF-8'?> <hudson> <disabledAdministrativeMonitors/> <version>2.346.3</version> <numExecutors>2</numExecutors> <mode>NORMAL</mode> <useSecurity>true</useSecurity> <authorizationStrategy class="com.michelin.cio.hudson.plugins.rolestrategy.RoleBasedAuthorizationStrategy"> <roleMap type="projectRoles"/> <roleMap type="globalRoles"> <role name="admin" pattern=".*"> <permissions> <permission>hudson.model.Hudson.Administer</permission> </permissions> <assignedSIDs> <sid>my-account@company.com</sid> </assignedSIDs> </role> </roleMap> <roleMap type="slaveRoles"/> </authorizationStrategy> <securityRealm class="org.jenkinsci.plugins.saml.SamlSecurityRealm" plugin="saml@2.333.vc81e525974a_c"> <displayNameAttributeName>user.givenname</displayNameAttributeName> <groupsAttributeName>user.memberof</groupsAttributeName> <maximumAuthenticationLifetime>259200</maximumAuthenticationLifetime> <emailAttributeName>user.mail</emailAttributeName> <usernameCaseConversion>lowercase</usernameCaseConversion> <usernameAttributeName>user.userprincipalname</usernameAttributeName> <logoutUrl>https://login.microsoftonline.com/removed-url/saml2</logoutUrl> <binding>urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect</binding> <advancedConfiguration> <forceAuthn>false</forceAuthn> <spEntityId>JenkinsSPTest</spEntityId> </advancedConfiguration> <idpMetadataConfiguration> <xml>removed_xml_data</xml> <url></url> <period>0</period> </idpMetadataConfiguration> </securityRealm> <disableRememberMe>false</disableRememberMe> <projectNamingStrategy class="jenkins.model.ProjectNamingStrategy$DefaultProjectNamingStrategy"/> <workspaceDir>${JENKINS_HOME}/workspace/${ITEM_FULL_NAME}</workspaceDir> <buildsDir>${ITEM_ROOTDIR}/builds</buildsDir> <markupFormatter class="hudson.markup.EscapedMarkupFormatter"/> <jdks/> <viewsTabBar class="hudson.views.DefaultViewsTabBar"/> <myViewsTabBar class="hudson.views.DefaultMyViewsTabBar"/> <clouds/> <scmCheckoutRetryCount>0</scmCheckoutRetryCount> <views> <hudson.model.AllView> <owner class="hudson" reference="../../.."/> <name>all</name> <filterExecutors>false</filterExecutors> <filterQueue>false</filterQueue> <properties class="hudson.model.View$PropertyList"/> </hudson.model.AllView> </views> <primaryView>all</primaryView> <slaveAgentPort>50000</slaveAgentPort> <label></label> <crumbIssuer class="hudson.security.csrf.DefaultCrumbIssuer"> <excludeClientIPFromCrumb>false</excludeClientIPFromCrumb> </crumbIssuer> <nodeProperties/> <globalNodeProperties/> <nodeRenameMigrationNeeded>false</nodeRenameMigrationNeeded> </hudson>
And below you can find the logout and login fields defined in the XML data I've stripped
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://login.microsoftonline.com/removed-url/saml2" /> <SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://login.microsoftonline.com/removed-url/saml2" /> <SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://login.microsoftonline.com/removed-url/saml2" />
Is logout with SAML 2.0 and HTTP-Redirect not working? Or is this user error?
Keep in mind I am testing on localhost, but given login works I'd be surprised if that had an effect on logout.