-
Type:
Bug
-
Resolution: Unresolved
-
Priority:
Major
-
Component/s: gerrit-trigger-plugin, jsch-plugin
-
Environment:Jenkins 2.387.1
Gerrit 2.14.6
Gerrit-Trigger -plugin-Version: 2.39.0
Jsch Plugin Version: 0.2.8-65.v052c39de79b_2
This had been all working until the latest plugin updates. And does work with newer Gerrit version instances.
Gerrit Trigger fails to connect Gerrit 2.14 - com.jcraft.jsch.JSchException: verify: false
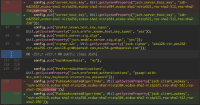
IOException: com.jcraft.jsch.JSchException: verify: false at com.jcraft.jsch.Session.connect(Session.java:330) at com.sonymobile.tools.gerrit.gerritevents.ssh.SshConnectionImpl.connect(SshConnectionImpl.java:196) Caused: com.sonymobile.tools.gerrit.gerritevents.ssh.SshException at com.sonymobile.tools.gerrit.gerritevents.ssh.SshConnectionImpl.connect(SshConnectionImpl.java:200) at com.sonymobile.tools.gerrit.gerritevents.ssh.SshConnectionFactory.getConnection(SshConnectionFactory.java:140) at com.sonymobile.tools.gerrit.gerritevents.ssh.SshConnectionFactory.getConnection(SshConnectionFactory.java:117) at com.sonymobile.tools.gerrit.gerritevents.GerritConnection.connect(GerritConnection.java:498) at com.sonymobile.tools.gerrit.gerritevents.GerritConnection.run(GerritConnection.java:404)
Cannot connect to Gerrit server! Host:
- relates to
-
JENKINS-69150 jsch plugin prevents Remote SFTP Plugin From Working on MacOS Monterey
-
- Closed
-