-
Type:
Bug
-
Resolution: Unresolved
-
Priority:
Major
-
Component/s: kerberos-sso-plugin
-
None
Hi,
We think this PR has broken our inbound-connected Windows Jenkins agents.
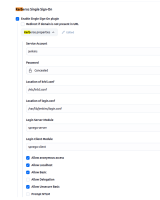
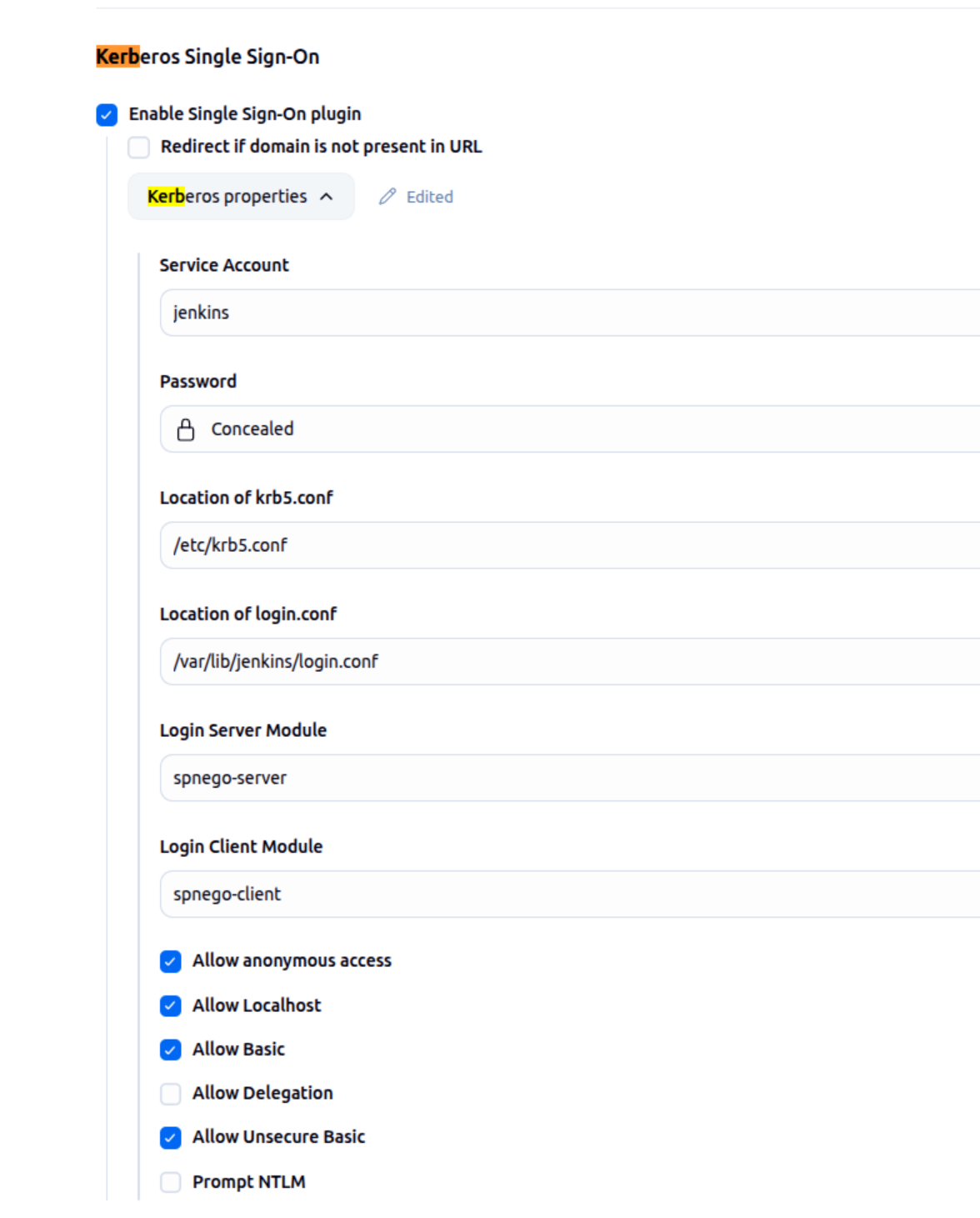
Our Jenkins controller is configured with the `Kerberos Single Sign-On` plugin and we allow our web browsers to authenticate via their Kerberos ticket.
We believe that the method below does not play well with authenticated Jenkins instances in which the `/login` endpoint would reply with 401 responses automatically. This is what we get with it:
INFO: Using C:\Users\ci-agent\jenkins\remoting as a remoting work directory
Jul 14, 2025 12:45:44 PM hudson.remoting.Launcher$CuiListener status
INFO: https://jenkins.internal.net/login is not ready: 401
We use SSO Kerberos and LDAP plugins for authentication. Is there a way to bypass this or perhaps modify the ping URL?
private Boolean pingSuccessful() throws MalformedURLException { // Unlike JnlpAgentEndpointResolver, we do not use $jenkins/tcpSlaveAgentListener/, as that will be // a 404 if the TCP port is disabled. URL ping = new URL(hudsonUrl, "login"); try { HttpURLConnection conn = (HttpURLConnection) ping.openConnection(); int status = conn.getResponseCode(); conn.disconnect(); if (status == 200) { return true; } else { events.status(ping + " is not ready: " + status); } } catch (IOException x) { events.status(ping + " is not ready", x); } return false; }
Our existing workaround is using the remoting JAR `version` 3273.v4cfe589b_fd83 - That one works flawlessly.